Cyber Security Audit
Overview
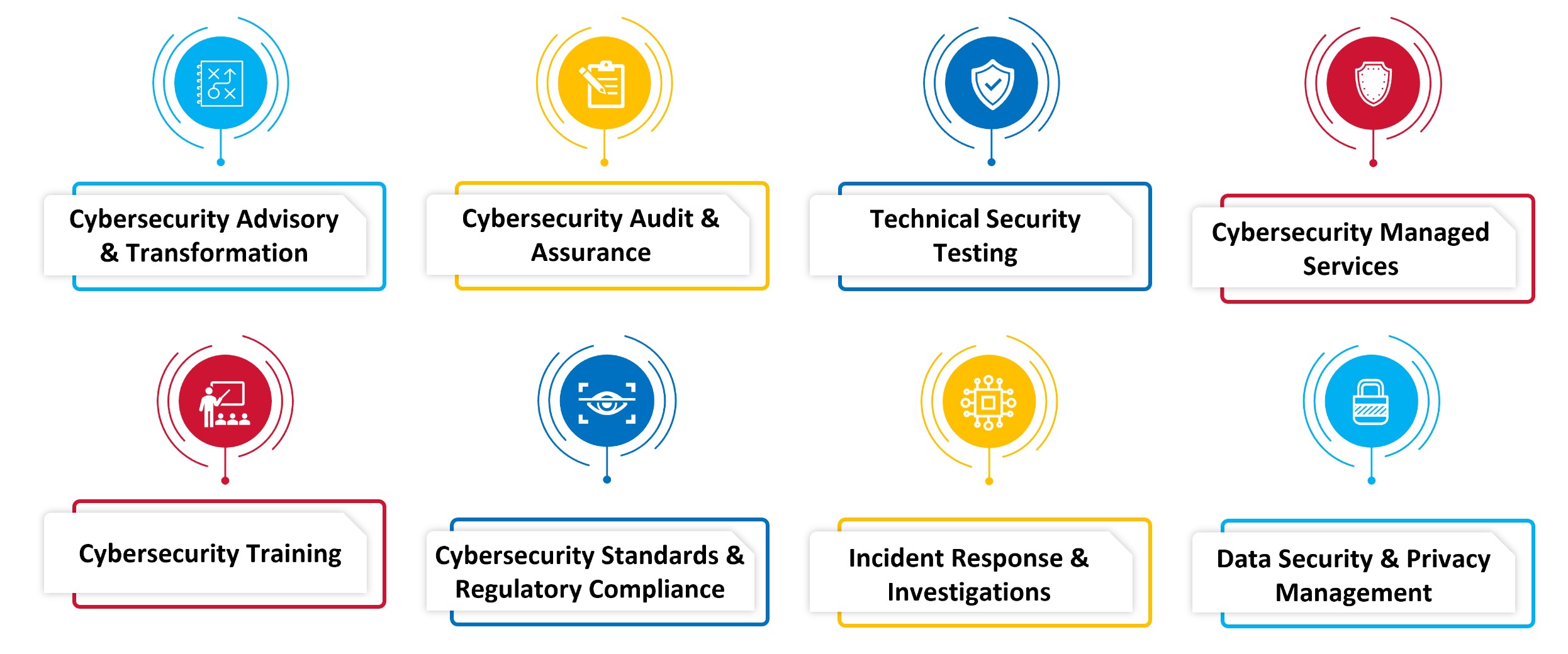
Through an unparalleled suite of cybersecurity services, we provide organizations with comprehensive solutions to ensure that most valuable information assets are protected. Our Cybersecurity services include:
Advisory & Transformation
Cybersecurity
Digital innovation has become the frontier of todays business in all sectors. With this increasingly digital existence comes a greater need to focus on cyber security. Not only to mitigate constantly evolving threats and improve business resilience but to unlock the growth which digitalization and disruptive technologies enables.
Further, Security and risk professionals need to make strategic decisions to protect the enterprise and deliver results; in support of the national level cybersecurity initiatives to improve the cybersecurity posture of the Kingdom in order to safeguard its vital interests, national security, critical infrastructures, high-priority sectors, and government services and activities in alignment with Vision 2030.
What we Deliver
- Cyber Maturity Assessments
- Develop Strategy & Roadmap
- Governance & Operating Model
- Cyber Risk Governance
- Information Security Policy and Processes
- Cyber Maturity Assessments
- Develop Strategy & Roadmap
- Governance & Operating Model
- Cybersecurity Architecture Blueprints and Implementation Assistance
ECOVIS has deep experience in Cybersecurity Advisory & Transformation services across industry verticals. Our transformations help our clients to reduce risk and enhance the effectiveness of their existing people, process and technology.
Technical Security Testing
Cybersecurity
Considering the recent sophisticated threats, organizations are expected to have data breaches. These can result in financial loss, regulatory sanction, and reputational damage. To assess and secure exposed attack surfaces, organizations are challenged to perform different security assessments to evaluate the effectiveness of their security controls. ECOVIS helps organizations assess, prepare and secure their IT infrastructure, software and third parties by combining classical ethical hacking principles and technical security reviews with advanced services in which we adopt a similar approach to that of an attacker.
What we Deliver
- Advance Ethical Hacking and Penetration Testing
- Advance Ethical Hacking and Penetration Testing
- Compromise Assessment
- Application Security Testing
- Social Engineering Testing
- Network Penetration Testing
- Wireless Penetration Testing
- Source Code Review
- API Security Testing
- Technical Configuration Reviews
Incident Response & Investigations
Cybersecurity
Help and expertise in planning for, and responding to, a significant cyber attack. It is advised to have this service in place as part of your business continuity and disaster recovery plan, as it is too late once a cyber attack has occurred.
What we Deliver
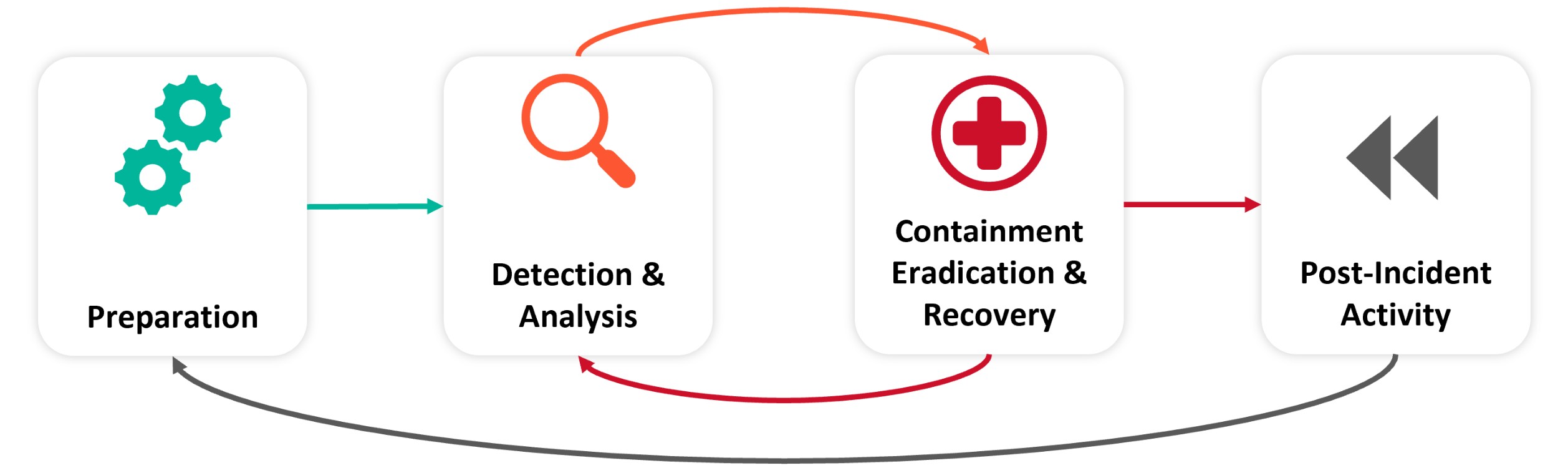
- Hunt for Active Attacks
- Stop a Breach and Perform Analysis
- Execute Crisis Management
- Recover Business Operations
- Response Readiness Assessment
- Post Incident Root Cause Analysis
Minimize the business impact of a cyber-attack by recovering quickly with an orchestrated resilience approach. We can help you build your incident response capabilities, respond to active breaches and bolster your security operations to detect and respond to attacks.
Regulatory
Compliance Services
In view of the ever-growing seriousness of cyber-attacks, several Kingdom wide cybersecurity initiatives, Standards, and Frameworks are been established across industry verticals to improve the cybersecurity posture and to safeguard its vital interests, national security, critical infrastructures, high-priority sectors, and government services and activities in alignment with Vision 2030.
What we Deliver
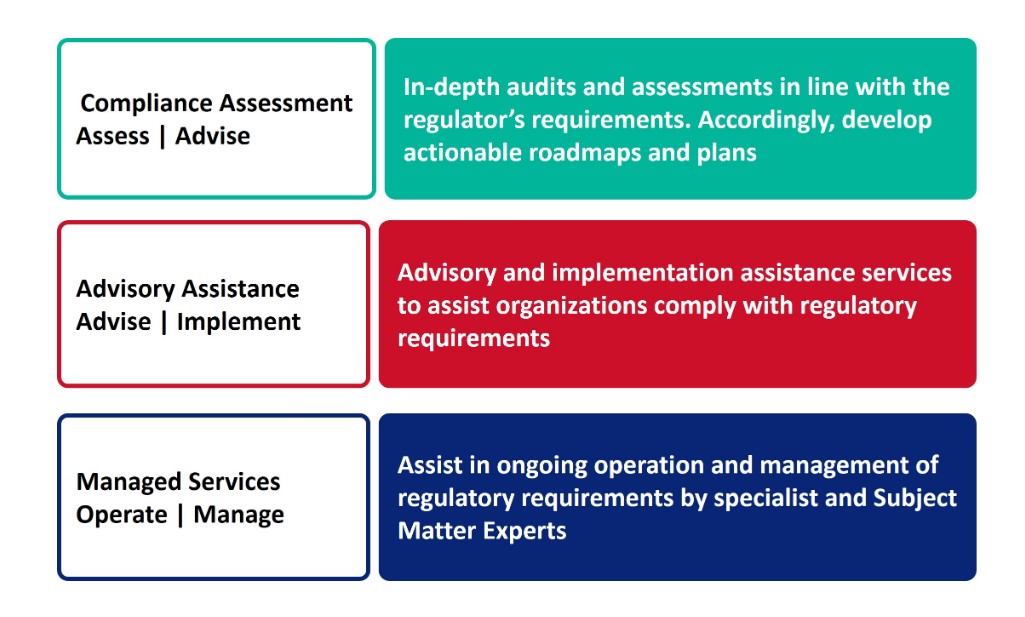
We at ECOVIS are professionally placed to help Organizations in complying with Cybersecurity Regulatory and Standards requirements. Our specialists can assist in achieving and maintaining all compliance obligations in the ever-changing regulatory environment.
- Cybersecurity Framework (CSF)- SAMA
- Essential Cybersecurity Controls – NCA ECC
- Members Technical Requirements Tadawul
- Business Continuity Management (BCM) framework – SAMA
- Cybersecurity guidelines for Capital Market Institutions- CMA
- Cybersecurity Regulatory Framework (CRF) – CITC
- National Data Governance Interim Regulations – NDMO